To use UNIX network tools,
If your choice of client is Mac or Linux, you can connect to isis.unc.edu using Terminal.
If you are using a Mac, connecting with terminal is somewhat similar to connecting with Windows.
If your choice of client is Windows, you can connect to isis.unc.edu using SSH.
We will use SSH for this example.
Start by opening a secure telnet connection to the ISIS server.
Use the terminal application on your Mac or Linux machine, or use SSH on your Windows machine. Each have their own version of the login. SSH uses ssh (the Secure Shell) to login, so that your username and password are not visible to other people on the campus network.
To login from your computer (it's the same here in the lab or elsewhere on your laptop):
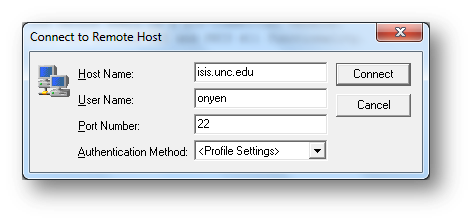
- Start the program (from your desktop, the Start menu, or from the Run dialog box)
- Select "Quick Connect", then enter isis.unc.edu in the dialog box and enter your onyen.
- Accept & Save the host key, if requested. (This is the encryption key that lets Isis identify itself).
- You will be prompted for your username & password; provide them.
- Once there, you are in the server so the rest of the commands will be common, no matter which kind of client application you used to get to the server. Find the $ prompt to get into a shell session and thus into UNIX.
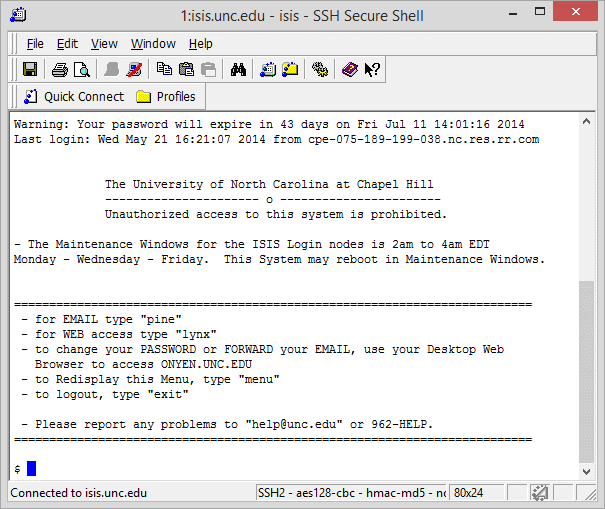
The $ is the UNIX prompt; bash $ may be a Linux prompt. But both will do the same things.
To logout when you're done (don't forget to do this!):
Type exit if you are at the shell prompt [the $] instead of the menu
or, select the logout option from the menu.
[top]
Internet tools available in UNIX and elsewhere (DOS, Windows)
Utilities available for UNIX/Linux and Windows machines, among others, include ping and traceroute.
ping
ping some URL like ping www.somedomainname.com
Ping sends a ICMP packet over the IP to check whether a host is alive, and how quickly a response is received.
On Isis and some other systems,
use ping -s www.somedomainname.com
then CNTL+C to cancel.
traceroute
traceroute www.somedomainname.com
traces the route your packets take to get to www.somedomainname.com.
The trace can be thrown off by firewalls or other systems that block some types of packets.
CNTL+C to cancel.
[top]
Try out Traceroute
We want to use Traceroute to see how long it takes to send a signal to a remote server and have it return to ISIS.
The traceroute program is used to determine the path that messages might take from one machine to another. Recall that any packet (message) sent on the Internet must go through some number of routers to get to its destination. Each link in this path is called a hop. Local traffic usually has very few hops (zero or 1 or 2) while long-distance traffic can take thirty or more hops before arriving. Traceroute lets us look at the path a message might take through this chain of routers to get to its destination.
In this example, I asked for a trace of a route from Isis to a location. I could see it first told me the site's IP address (expressed in numbers) and then showed me all the jumps from ITS's ISIS server through switches at CiscoKid, on to RTP, then onto the Internet backbone through several different backbone providers before it ran into routers with masked addresses at the tenth step.
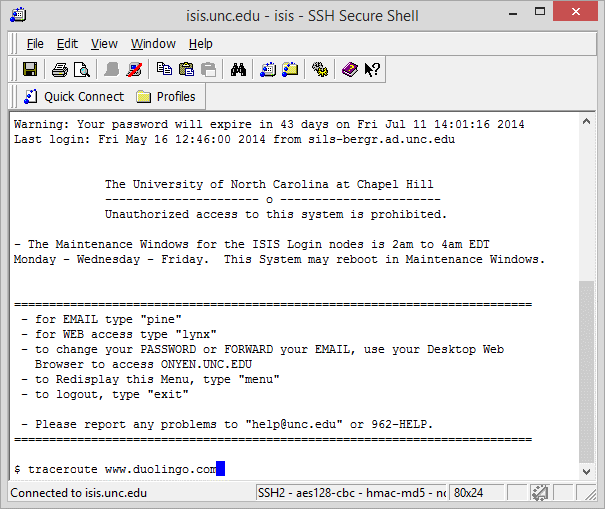
Try it out on sites you are curious about. Look at the path the connection follows and how long each segment takes. When you are finished, type in the command exit and then select option 8 to close your link to ISIS
[top]
The above procedure allows you to run traceroute on a Unix server, but you can also run it on a Windows PC
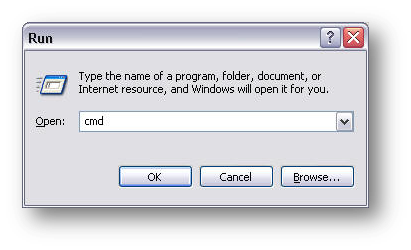
The DOS way to run Traceroute is to go to start and then open the run dialog box. Then type in cmd for a command prompt. Once you have the command prompt, type the command tracert followed by the internet address.
This time, however, the trace will go from your client, through your ISP, and then on to it's destination. The difference is that when you used SSH you were tracing from Isis (because you were using a Telnet application), but in this case you are using a client application and tracing from your client computer.
Online tools
There are online traceroute tools, as well as additional explanations of the command. In fact, there are lots of additional explanations.
[top]

