Video 6: Encryption and public keys
Encryption
Data is kept secret through encryption
scrambling to hide original text
Encryption is a process wherein information is encoded, hiding the original text so that outside parties are unable to decipher its meaning without access to the key or advanced decoding software. Encryption uses algorithms that turn information into symbols or text that can only be interpreted if transferred back into plaintext, or decrypted, thus making it inaccessible by potential interceptors.
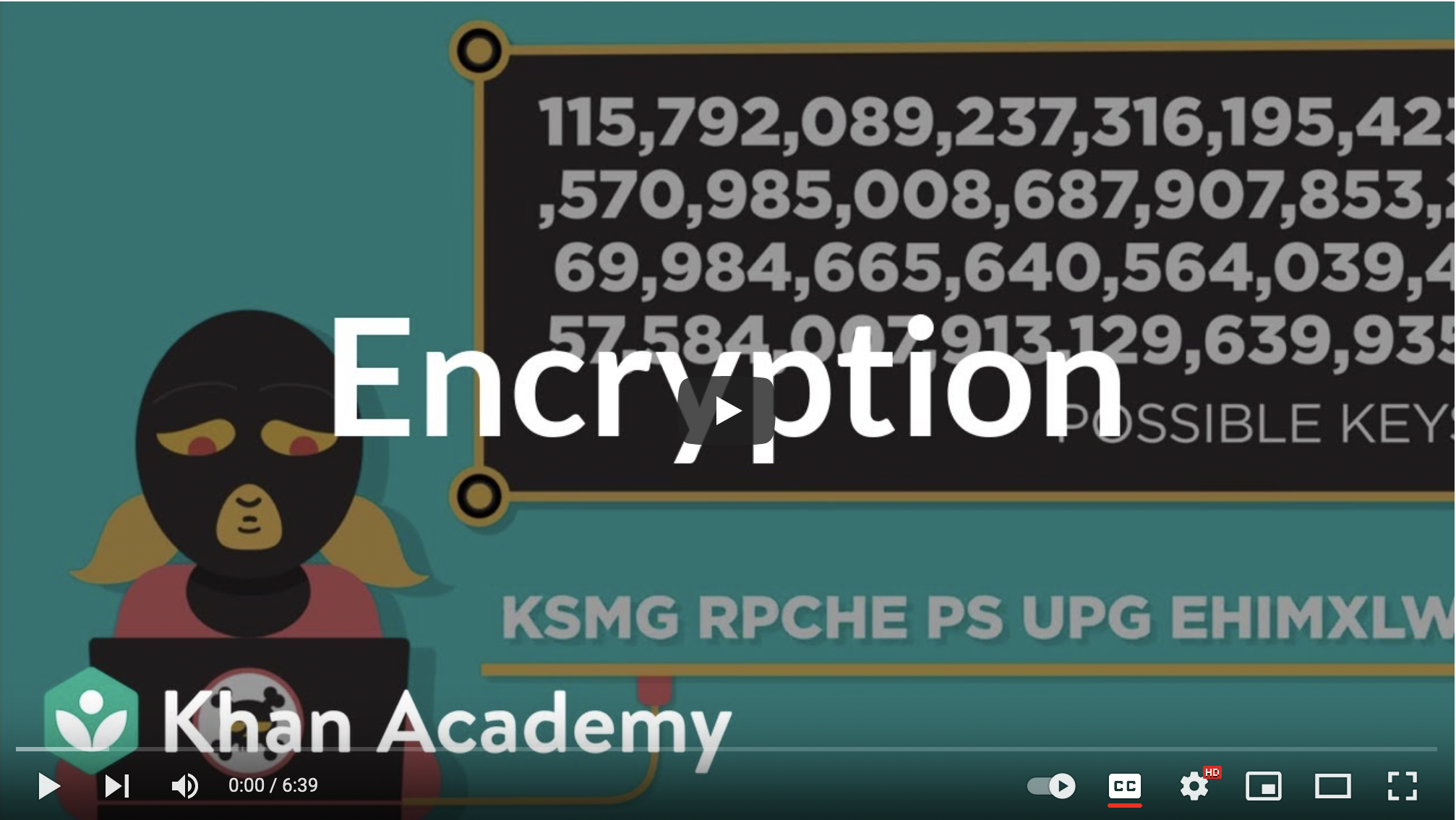
Keys and 256 Bit Key
A key is something that only the sender and receiver know and it allows the reader to unlock an encrypted message.
256 bit key is a modern, advanced encryption key with similar ideas to the Caesar's Cipher. It has a large key length of 256 bit and it encrypts messages and data. The reason it is so effective is that, because of it's large size, it would take millions of years for a modern day computer to test all of the possibilities for the key. As computers become faster, a larger key might be necessary.
Public and Private Key Encryption
In public and private key encryption, a public key open to anyone is used to encrypt the data, but the only way to decrypt the data is with the matching private key, which is only distributed to those that are supposed to be able to see the decrypted information. The exclusivity of owning the matching private key is what provides the security and confidentiality of this system.
Caesar cipher Caesar's Cipher and Algorithm
Caesar’s Cipher is a way in which we can encrypt messages so a person without the code cannot read the message. A basic description of Caesar’s Cipher is creating a password, such as 3, and then add or subtract three to every single letter in the message so “hello” will end up being “khoor”. However, because there are only 26 letters in the alphabet, it would be easy to try 0-26 and eventually crack the code. In response to this, an algorithm was developed which randomly generates a different number for every single letter in the message. Therefore, the “h” in “hello” could have a 7, the “e” could have a 2, etc. There is a 10 bit encryption which would leave the encrypted message with 10 billion possible key solutions or a 256 bit key encryption, which is impossible for even a computer to hack without the code. This is an extremely useful security tool for which we will continue to expand in the future.
Symmetric Encryption
A type of encryption when the secret key has to be agreed on ahead of time by two people in private. Sender and receiver share the same key to unlock the cypher. However, there is a problem with sharing the key over the internet because it is public.
Asymmetric Encryption
A type of encryption where there is a public key that is shared with anybody and a private key that is not shared. Public key is used to encrypt the data, but it can only be viewed by someone who has a private key. Pretty much, you can send each other encrypted mail but only the computer with the secret key that’s not shared can open it.
Security protocols SSL and TLS signified by https or lock symbol
SSL and TLS prevent stealing of information
Protocols to ensure all data sent is encrypted. Browsers are now warning users when a login is not encrypted.
https://serverguy.com/security/google-forcing-ssl-certificate-websites/
https://www.thesslstore.com/blog/deadline-install-ssl-certificate-google-marks-not-secure/
Active when lock is next to http
encryption, Caesar's Cipher, algorithm, key, 256 bit keys ⇒ random key generator, symmetric encryption, asymmetric key, private key, public key
Cybersecurity viruses, DDOS attacks, phishing, hacker, botnet